Efficient use of security solutions, optimized tool usage,
and technical know-how present a new standard
for problem-solving with PLURA.
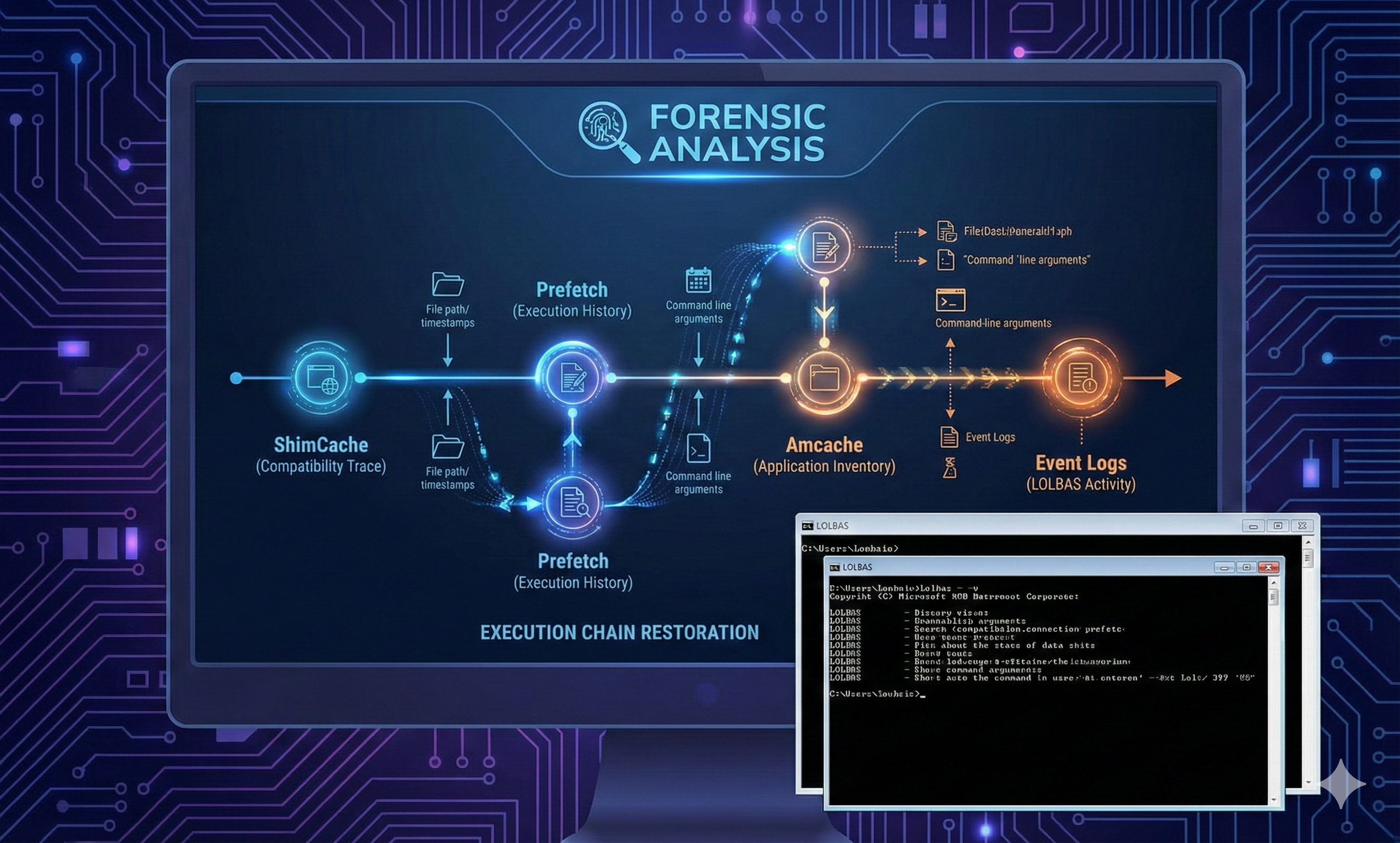
Sysmon → Prefetch → ShimCache → Amcache: Practical Guide to Reconstructing Execution Chains (Including LOLBAS Log Correlation)
📌 This article has one goal.
We don’t stop at “Was the malicious file executed?” — we go one step further:
✅ “Who (parent) → executed what (child) →...
Do You Really Need NAC (Network Access Control)? Here’s a More Efficient Alternative
📖 Is a NAC (Network Access Control) solution really necessary? A practical assessment
Read moreObjective: In information security, proactive measures are...