“Security is not a product, but a process.” — Bruce Schneier
And a single vulnerability can bring down the entire system.
Latest Posts
PLURA Is a New Milestone in Cybersecurity in the AI Era
🧭 Conclusion of This Article (3-Line Summary) In the LLM era, rapidly emerging products fall into two categories: (1) LLM Wrappers and (2) AI...
Read moreOdido 6.2 Million Customer Data Breach: Social Engineering Attack Penetrating CRM via Phishing and IT Support Impersonation
Dutch telecom operator Odido announced a customer personal data breach. The incident reportedly began with phishing emails + IT support impersonation...
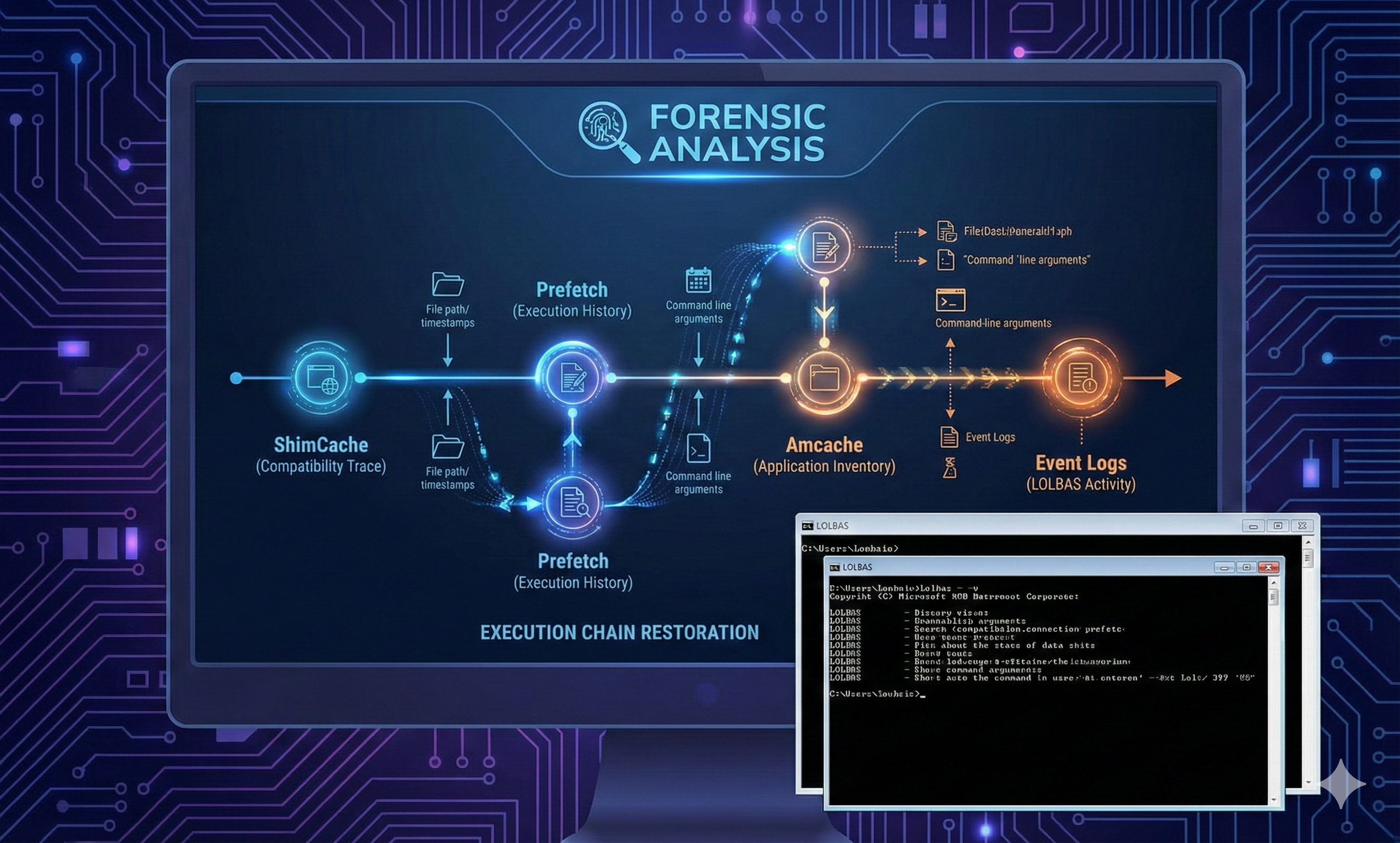
Read moreSysmon → Prefetch → ShimCache → Amcache: Practical Guide to Reconstructing Execution Chains (Including LOLBAS Log Correlation)
📌 This article has one goal. We don’t stop at “Was the malicious file executed?” — we go one step further: ✅ “Who (parent) → executed what (child) →...
Read more[Policy Proposal] South Korea's Hacking Problem Stems from Government Certification Systems
Abolishing Korea’s Information Security Certification System and Implementing a Complete Attack Response Strategy The government-mandated security...
Read more[Report] Why the ISMS Certification System Is No Longer Valid
Report on the Technical Irrationalities and Real-World Gaps in Korea’s Information Security Certification System Overview and Background Korea’s...
Read morePLURA Does the Unimaginable
🎬 Famous Quote from The Imitation Game “Sometimes it is the people no one imagines anything of who do the things that no one can imagine.” “It is...
Read moreHow to Check If a Hacking Attack Is Happening Right Now?
“Invisible hacking threats could be happening right now.” Hacking doesn’t usually happen all at once. 🔓 It often penetrates quietly and deeply, likely...
Read moreIf You Deploy SOAR, Then What? No Real Automated Response If It Can’t Act
📉 SOAR solutions typically receive security events from SIEM and then carry out automated responses. Yet many organizations report: “We deployed SOAR...
Read moreSo You Deployed a SIEM—Now What? If You Can’t Collect or Analyze Logs Properly
📉 Many companies consider deploying Unified Log Management or a SIEM. However, there’s a critical question: Are you actually collecting your logs? And...
Read moreComprehensive Summary of the SKT USIM Hacking Incident: Causes, Impact, and Response Measures
Key Summary The SK Telecom HSS breach, confirmed on April 18, 2025, exposed USIM authentication data of up to 23 million users. On April 28, SKT...
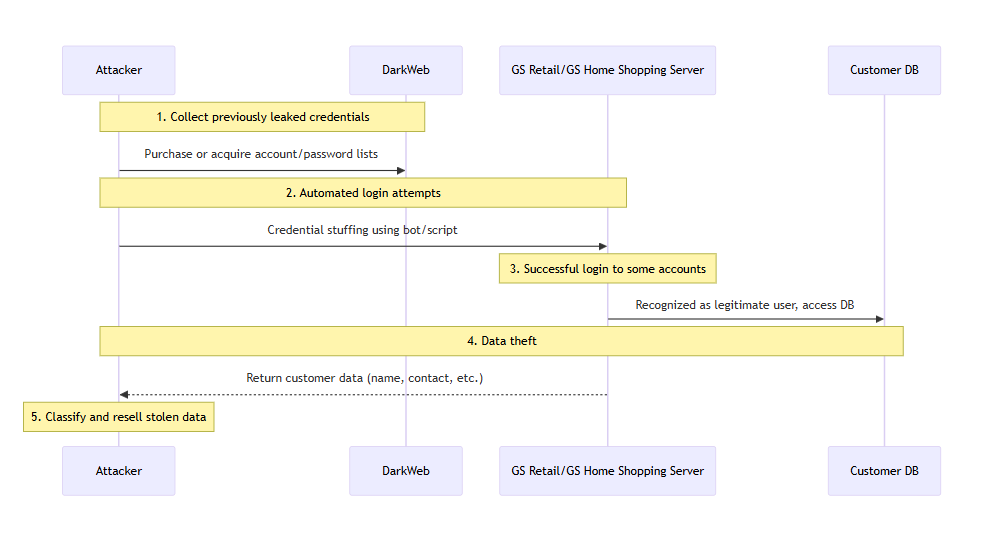
Read moreCredential Stuffing Attack Cases: GS Retail & GS Home Shopping
In January–February 2025, a credential stuffing attack occurred on the online services of GS Retail and GS Home Shopping, leading to the leakage of...
Read moreDo You Really Need NAC (Network Access Control)? Here’s a More Efficient Alternative
📖 Is a NAC (Network Access Control) solution really necessary? A practical assessment Objective: In information security, proactive measures are...
Read moreTraditional SOC vs. PLURA-XDR-Driven SOC: From Reactive Response to Proactive Defense
⛑️While both a traditional Security Operations Center (SOC) and a PLURA-XDR-Driven SOC serve the common goal of protecting enterprise environments,...
Read moreStrategies for Responding to Zero-Day Attacks
🕵️♂️ As cyber threats become increasingly sophisticated, traditional signature-based detection methods alone are no longer sufficient. Zero-day...
Read moreWhy Is Full Web Log Analysis Important?
🔍 Recent cyber threats have become more sophisticated, often unfolding in stealthy, multi-stage sequences. Instead of focusing solely on specific...
Read moreDo We Really Need NIPS/NDR, Even for SMEs or Large Enterprises?
⛑️Focusing on small- to mid-sized enterprises (SMEs), we revisit the question of whether NIPS (Network-based Intrusion Prevention System) and NDR...
Read moreIntroduction to Preventing Data Exfiltration via Web Attacks
🧑💻 The Ultimate Goal of Hacking: Data Exfiltration Customer records, personal information, or a company’s critical assets are typically the prime...
Read moreLimitations of NDR: An Unsolvable Mission
📡 NDR (Network Detection and Response) has become a staple in network security technologies, yet it faces inherent limitations. From structural...
Read moreUnderstanding Intrusion Prevention Systems (IPS)
🛡️An Intrusion Prevention System (IPS) is a critical technology for proactively detecting and blocking security threats at both the network and host...
Read moreIs Investigating Hacking Through Log Analysis Just a Myth?
When a hacking attack occurs, most people conduct log analysis. They believe that through log analysis, they can figure out: How the hack happened...
Read more[Q&A] Exploring Request Body Log Analysis in Splunk with ChatGPT
💬 Can Splunk Analyze Web Request Body Logs? “This Q&A is summarized with ChatGPT’s assistance. The answers reflect ChatGPT’s translation and...
Read moreUsing the Advanced Audit Policy from a MITRE ATT&CK Perspective with ChatGPT
This content is a summary of a Q&A session with ChatGPT. There have been no arbitrary modifications to the portions written by ChatGPT.
Read moreWhy Do We Analyze GET/POST Logs?
What is HTTP? HTTP (Hypertext Transfer Protocol) is a protocol that enables communication between clients and servers. It operates on a...
Read more

![[Policy Proposal] South Korea's Hacking Problem Stems from Government Certification Systems](https://blog.plura.io/cdn/column/policy-proposal.png)
![[Report] Why the ISMS Certification System Is No Longer Valid](https://blog.plura.io/cdn/column/policy-proposal-example-useless.png)









![[Q&A] Exploring Request Body Log Analysis in Splunk with ChatGPT](https://blog.plura.io/cdn/column/splunk_request_body_analysis.jpg)

